Verifiable credentials represent an evolution in how we handle and authenticate personal information online. At the core, they are digital counterparts of the physical credentials we use daily, like driver's licenses, university degrees, or passports. These digital credentials encompass similar data elements: identifying information about the subject, the issuing authority, the type of the credential, attributes asserted about the subject, how the credential was derived, and any constraints like expiration dates.
The main distinction is the incorporation of technologies like digital signatures, which enhance the credibility of these credentials by making them tamper-evident and more trustworthy. Not only can holders of verifiable credentials generate and share cryptographically secure presentations, but these digital forms can also be transmitted rapidly, offering convenience, especially in remote trust-establishment scenarios.
However, the digital nature of these credentials raises valid privacy concerns due to the persistence and easy aggregation of digital data, hence the emphasis on balancing accessibility with privacy preservation in their design and use.
Elements of Verifiable Credentials
1. Holder
A holder is an entity that possesses one or more verifiable credentials and has the capability to generate verifiable presentations from them.
Examples:
Students: Holding credentials about their educational qualifications or identity.
Employees: Holding credentials about their employment status or work-related qualifications.
Customers: Holding credentials about their purchase history or loyalty program status.
2. Issuer
An issuer is an entity responsible for asserting claims about one or more subjects. They create a verifiable credential from these claims and transmit the verifiable credential to a holder.
Examples:
Corporations: Issuing verifiable certificates (credentials) on blockchain about an employee's position or achievements.
Non-profit Organizations: Issuing credentials about membership or participation in events.
Trade Associations: Issuing credentials about certifications or memberships.
Governments: Issuing credentials such as passports or driving licenses.
Individuals: Issuing personal attestations or claims about another individual.
3. Subject
A subject is an entity about which claims are made. The holder of a verifiable credential can often be the subject, but there are scenarios where they are different.
Examples:
Human Beings: Such as an individual's age, nationality, or qualifications.
Animals: For instance, a pedigree or vaccination record.
Things: Assets, properties, or any non-living entities that require a verifiable claim.
Special Cases: A parent might hold a verifiable credential for their child, wherein the child is the subject. Similarly, a pet owner might hold the verifiable credentials for their pet.
4. Verifier
A verifier is an entity that receives one or more verifiable credentials, optionally within a verifiable presentation, for the purpose of processing and verifying the authenticity of the claims. In simple terms, Verifier is responsible for verifying digital credentials.
Examples:
Employers: Verifying the educational qualifications of a potential hire.
Security Personnel: Checking the verifiable credentials to grant access.
Websites: Authenticating users before providing services or access to information.
5. Verifiable Data Registry
This is a system or a role that facilitates the creation and verification of identifiers, keys, and other vital data, such as verifiable credential schemas, revocation registries, issuer public keys, and more. It is integral for the successful use and verification of verifiable credentials.
Core Data Model
1. Claims
A claim is a statement made about a subject. The subject, in this context, is an entity about which claims can be made. This can be visualized as a subject-property-value relationship. Using this model, one can represent a variety of statements. For instance, a claim can express that "Pat is an alumnus of XYZ University'." Claims can also be integrated to depict a comprehensive information graph about a subject.
2. Credentials
A credential constitutes one or multiple claims made by a particular entity. It may come with an identifier and metadata providing details about the properties of the credential, including the issuer, expiration date and time, representative image, public key for verification, revocation process, and more. The issuer may authenticate this metadata. If the claims and metadata in a credential are tamper-proof, ensuring cryptographic verification of its issuer, it's called a verifiable credential. Examples include digital ID cards, birth certificates, or educational diplomas.
3. Presentations
Privacy enhancement is central to the data model. Consequently, the holder must be able only to reveal relevant parts of their identity as suited for specific situations. This selective portrayal is termed a verifiable presentation. Such presentations articulate data from one or more verifiable credentials so that the data's authorship remains provable. Directly presented verifiable credentials transform into verifiable presentations. Data forms that stem from verifiable credentials and are cryptographically provable, even if they don't inherently contain verifiable credentials, might also be recognized as verifiable presentations.
Here’s a diagram to better understand the working of Verifiable Credentials:
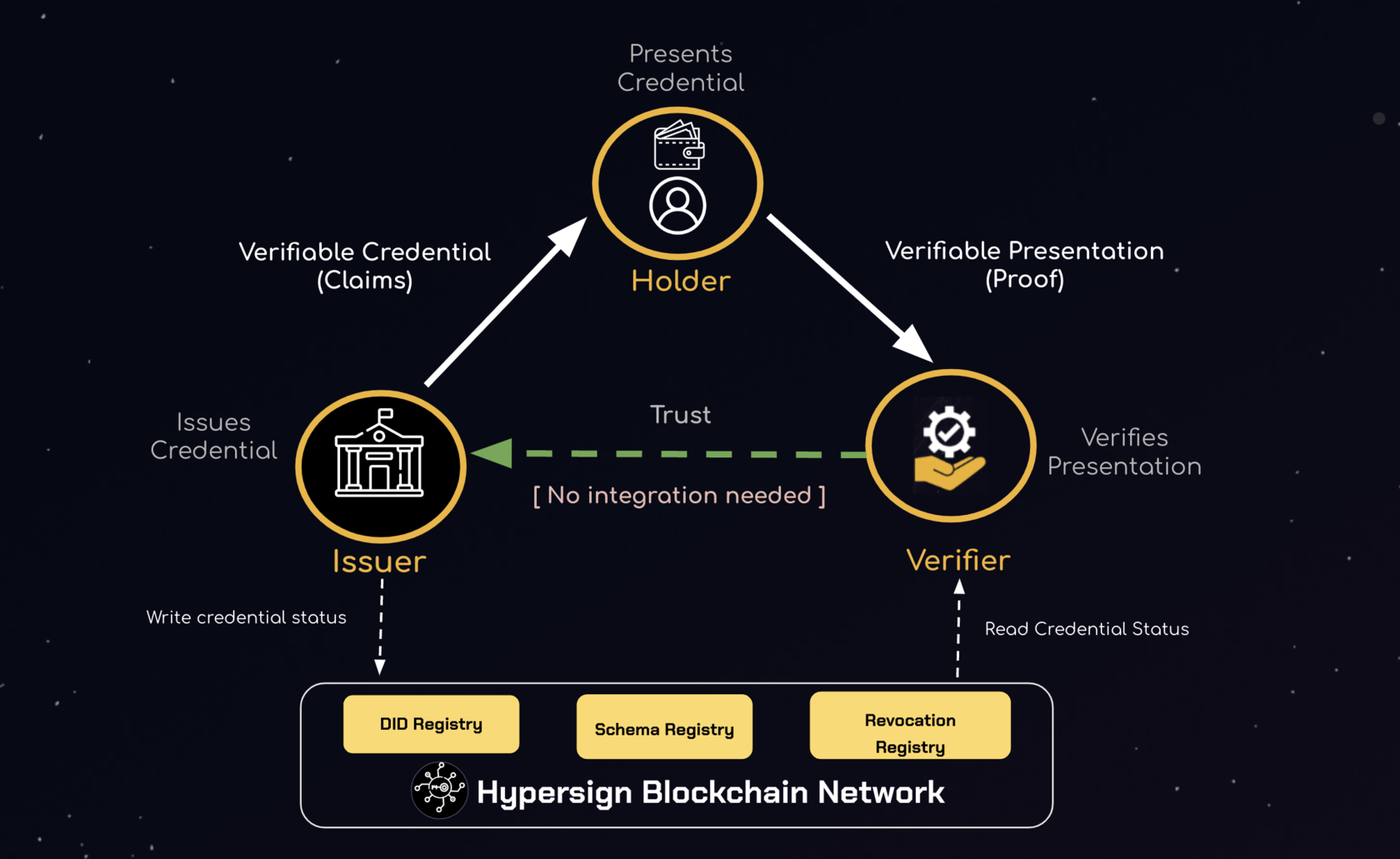
A user/subject sends data requests for a verifiable credential from an issuer. The issuer verifies these data/claims and issues a verifiable credential by writing the attestation on the blockchain (as shown in the above figure, to be used later to verify credential revocation) and then sends the verifiable credential to the user. The user may store the credential in something called an Identity Wallet - an app designed to store verifiable credentials securely.
Whenever a user needs a service from a service provider, the user presents the verifiable credential in the form of a verifiable presentation to the service provider/verifier.
The service provider verifies the following details before providing the service:
- Is this verifiable credential actually coming from a trusted issuer?
- Does this user actually own this credential?
- Was this credential tampered with?
- Was this credential revoked by the issuer?
Note:
A verifiable credential has the signature of the issuer, but a verifiable presentation contains the signatures of both the issuer and the user.
How does Credential Revocation work?
Whenever a credential is issued to a user, its claims are attested and stored on the blockchain in the revocation registry. This aids in credential revocation. If an issuer wants to revoke a credential, they can do so merely by changing the status of the credential on the blockchain. The issuer doesn't need the user’s data for this purpose.
How do Verifiable Credentials assist in compliance with GDPR or DPDP?
Ideally, no user’s data needs to be stored on the issuer's end; instead, data is verified, claims are attested on the blockchain, and then the data is returned to the user as a verifiable credential to be stored in the identity wallet. This helps issuers not only comply with regulations such as GDPR or DPDP’23 but also reduces the risk of data management.
How do Verifiable Credentials help to avoid data breaches?
As discussed in the previous section, it's not required for an issuer to retain and store a user’s personal data. This means a lot of user data doesn't need to be aggregated in one location or database. Hence, issuers' systems are not honeypots for hackers. If a hacker wants to obtain all user data, they would have to attack individual user’s ID wallets, which is practically impossible. This way, issuers don't face the risk of handling users' data and thus avoid potential data breaches or hacks.
Use Cases of Verifiable Credentials
Verifiable Business Cards
As business networking evolves, the shift from traditional to digital business cards presents both opportunities and challenges, notably increased risks of identity theft. Hypersign, harnessing its decentralized identity platform, enables users to create, manage, and distribute their unique digital identities. This system allows for real-time information updates and revocation of credentials, ensuring accuracy and security. Moreover, Hypersign's capability for public verification of these digital cards offers a safeguard against identity theft and related scams. As a testament to its potential, Hypersign has developed an MVP for verifiable business cards, providing a practical application of this use case. For an in-depth understanding and a guide to creating one, refer to this blog.
Age Verification for Liquor Distribution
One of the prime concerns for liquor distributors or sellers is ensuring that the product doesn't fall into the hands of underage individuals. By using verifiable credentials, age verification can be done seamlessly and securely. Instead of showing physical ID, which may be falsified or tampered with, customers can present a digitally verifiable credential that proves their age. For sellers, this can assure them that they're not inadvertently violating age-restriction laws. For consumers, it allows for a quicker and more private transaction, as they don't need to disclose any information beyond their age. We at Hypersign are doing a pilot of this at the Moto GP Bharat 2023 with one of the biggest players in the physical event space in India called AtomX; details are below:
Portable Game Assets
In the gaming industry, players often accumulate achievements, skills, in-game assets, and other credentials. By integrating verifiable credentials into games, it becomes possible for players to carry over certain achievements or digital assets from one game to another or even from one gaming platform to another. This means a player's achievements aren't confined to one ecosystem but can be recognized across multiple platforms. It not only enhances the gaming experience by providing continuity but also ensures that a player's progress and achievements are genuinely theirs, given the verifiable nature of these credentials. Here’s our work on this use case.
Regulated Launchpads and Decentralized Exchanges
DEX and launchpads facilitate the trade of cryptocurrencies and the introduction of new decentralized projects. Verifiable credentials can be employed to ascertain the legitimacy of traders or projects. For traders, this can ensure compliance with Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations without sacrificing their privacy. For new projects on launchpads, verifiable credentials can provide assurance to potential investors about the authenticity of the project's founders, team members, or advisors. This can foster a safer and more trustworthy decentralized trading and investing environment. Here’s our work on this use case.
Education and Training
Verifiable credentials can be used to verify qualifications, certifications, and achievements in education and training. For example, universities can issue digital diplomas that potential employers or other institutions can instantly verify. This can save time and hassle for both students and employers, and it can also help to prevent fraud.
Supply Chain Management
Verifiable credentials can be used to track the origin, authenticity, and quality of products in the supply chain. For example, a farmer could use a Verifiable Credential to prove that their produce was grown using organic methods. This can help to ensure that consumers are getting the products they expect, and it can also help to protect businesses from counterfeiting.
Financial Services
Verifiable credentials can be used to verify the identity of customers, to authenticate transactions, and to prevent fraud. For example, banks could use Verifiable Credentials to confirm the identity of customers without requiring them to visit a branch physically. This can make it easier for customers to do business with banks, and it can also help to protect banks from fraud.
Healthcare
Verifiable credentials can be used to securely store and share medical records between healthcare providers and patients. For example, patients could have access to their own medical records through Verifiable Credentials that they control. This can help to improve the quality of care that patients receive, and it can also help to protect patients' privacy.
Human resources
Verifiable credentials can be used to verify employment history and qualifications during the hiring process. For example, job applicants could provide verified information about their previous employment or educational achievement using Verifiable Credentials. This can help employers to make more informed hiring decisions, and it can also help to protect employers from liability.
About Hypersign
Hypersign is an innovative, permissionless blockchain network that manages digital identity and access rights. Rooted in the principles of Self-Sovereign Identity (SSI), Hypersign empowers individuals to take control of their data and access on the internet. It provides a scalable, interoperable, and secure verifiable data registry (VDR) that enables various use cases based on SSI. Built using the Cosmos-SDK, the Hypersign Identity Network is recognized by W3C (World Wide Web Consortium), promoting a seamless and secure identity management experience on the Internet.
Contact us today to understand the nuances of the decentralized identifier and their real-world application at meet.hypersign@gmail.com. We can help you issue blockchain-powered credentials in no time!



















