TL;DR Zero-knowledge proofs (zk proofs) enable secure validation without revealing underlying data. They're used interactively or non-interactively (zk-SNARKs) and offer superior privacy, security, and data minimization. Hypersign employs Cross-Chain privacy preserving KYC using Zero-knowledge proofs and Interblockchain Communication (IBC).
What is Zero Knowledge Proof?
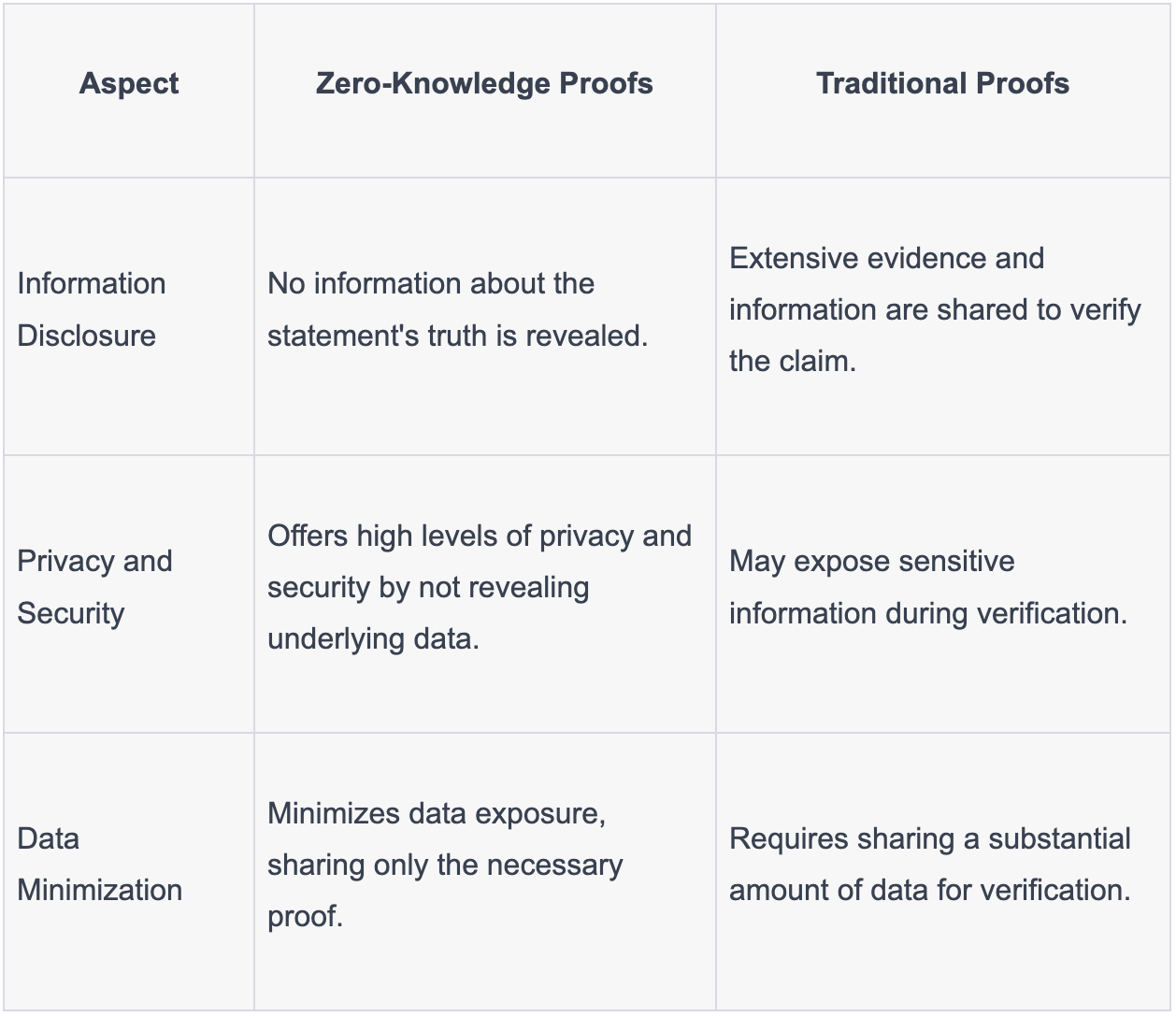
In the realm of cryptography and secure communication, zero-knowledge proofs (zk proofs) stand as a groundbreaking concept that allows one party to prove the truth of a statement to another party without revealing any information about the statement itself. In essence, zero-knowledge proofs enable the verifier to confirm the validity of a claim without gaining any knowledge beyond the claim's truthfulness.
Zero-Knowledge Proofs vs. Traditional Proofs - Key Differences
How does zero-knowledge proofs work?
Zero-knowledge proofs operate through a complex cryptographic process where a prover aims to convince a verifier of the validity of a statement without revealing the actual data. In an interactive scenario, the prover and verifier engage in multiple rounds of communication, with the prover crafting a proof that demonstrates their knowledge of a solution. The verifier challenges the prover with queries, and correct responses ensure the prover's knowledge. In non-interactive proofs, like zk-SNARKs, a one-time setup phase generates cryptographic parameters. The prover creates a succinct proof and sends it alongside the statement, while the verifier, using the parameters, checks the proof's validity without requiring further communication. This elegant mechanism, supported by advanced mathematics and cryptographic primitives, enables privacy-preserving authentication and transactions within decentralized systems like blockchain while safeguarding sensitive information.
Types of Zero-Knowledge Proofs
Interactive Zero-Knowledge Proofs
In this type, the prover interacts with the verifier to demonstrate knowledge of a specific value without revealing it. Examples include Schnorr and Fiat-Shamir identification protocols.
Non-Interactive Zero-Knowledge Proofs (zk-SNARKs)
Non-interactive zero-knowledge proofs eliminate the need for ongoing interaction between the prover and verifier. Instead, the prover generates a succinct proof and provides it to the verifier, who can then validate the proof's correctness without further exchanging information.
Advantages of Zero-Knowledge Proof
Privacy and Security
Zero-knowledge proofs enable individuals to prove possession of specific information without actually revealing that information. This has profound implications for privacy, allowing for secure authentication and authorization processes without sharing sensitive data.
Data Minimization
Traditional authentication methods often involve sharing a substantial amount of data for verification. Zero-knowledge proofs drastically reduce data exposure, only disclosing the necessary proof without revealing underlying information.
Decentralized Identity
Zero-knowledge proofs can play a vital role in decentralized identity systems, allowing individuals to prove their identity without sharing unnecessary personal information. This aligns with the principles of self-sovereign identity and enhances user control over data.
Fraud Prevention
By allowing one party to prove knowledge of specific information without revealing the information itself, zero-knowledge proofs can be applied to prevent fraud and ensure compliance in various domains.
Use cases related to zero-knowledge proofs on Blockchain
Transaction Privacy and Confidentiality
ZKPs enable transaction privacy by allowing users to prove the validity of transactions without revealing the transaction details. This use case is particularly relevant in public blockchains like Ethereum, where ZKPs can be used to create confidential transactions. These transactions ensure that the sum of inputs and outputs remains balanced while keeping the transaction amounts hidden from public view. This use case enhances privacy for individuals using cryptocurrencies while still ensuring the integrity of the blockchain.
Identity and Authentication
ZKPs have transformative implications for identity and authentication systems. They allow individuals to prove attributes or credentials without disclosing the underlying data.
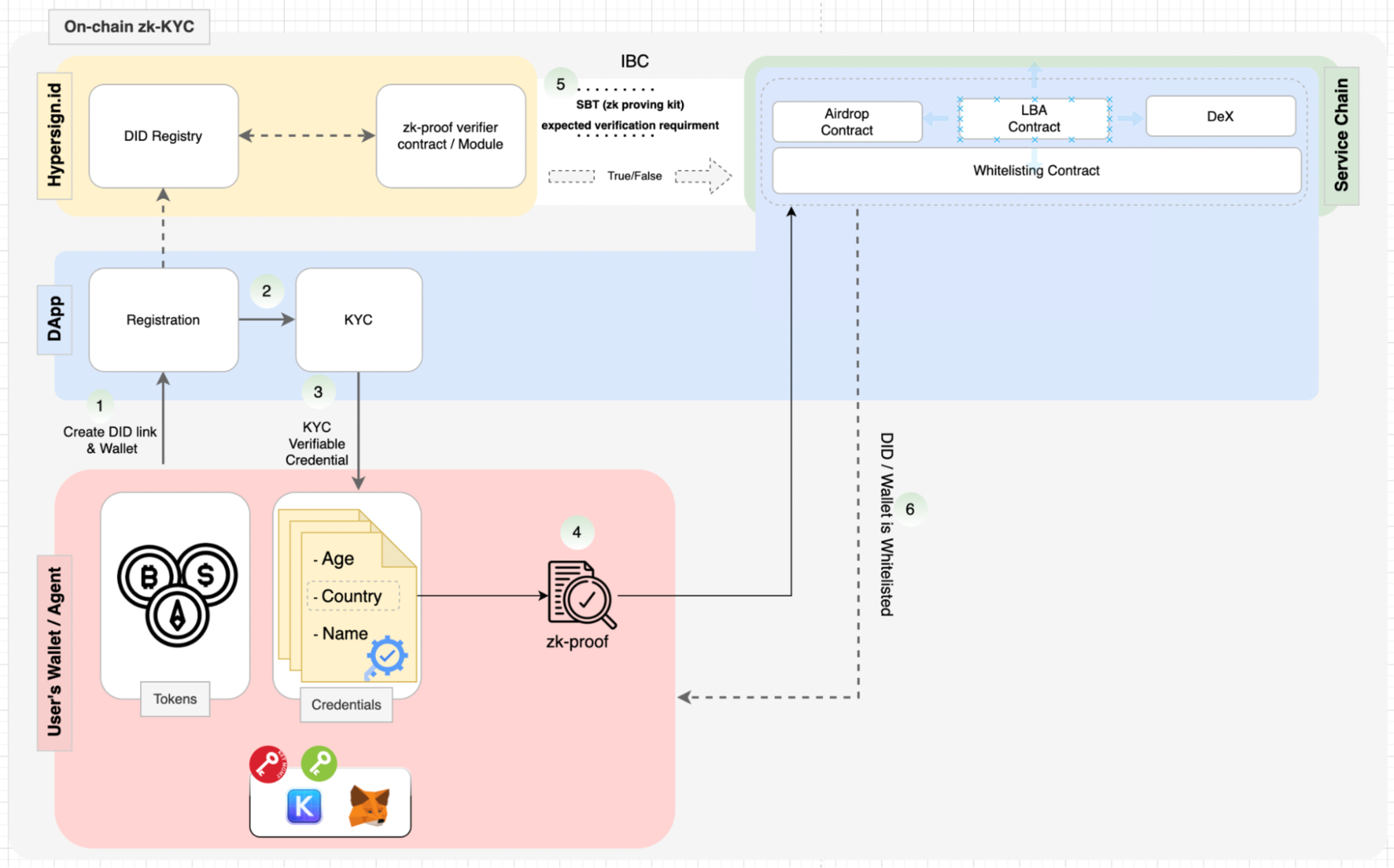
For instance, Hypersign is spearheading the development of a Cross-Chain privacy preserving KYC using Zero-knowledge proof (ZKPs) and Interblockchain Communication (IBC) for Cosmos. This solution empowers individuals to control their digital identities while securely sharing selective attributes for specific purposes. Leveraging ZKPs, Hypersign enables users to prove their eligibility for certain services or transactions without revealing sensitive information. The implementation seamlessly integrates ZKPs with self-sovereign identity protocol, resulting in an innovative approach to privacy-preserving KYC and data interaction.
Here’s a diagram of how it works:
Scalability Solutions
ZKPs play a key role in addressing blockchain scalability challenges. In Layer 2 scaling solutions, such as zk-Rollups, ZKPs are used to aggregate and validate multiple transactions off-chain and then submit a succinct proof to the main blockchain. This approach significantly reduces the computational load on the main blockchain, leading to faster and more efficient transaction processing. Scalability solutions powered by ZKPs are particularly important for public blockchains aiming to handle many transactions without compromising decentralization or security.
These use cases highlight the versatility of zero-knowledge proofs in enhancing privacy, security, and efficiency within blockchain ecosystems. By enabling cryptographic proofs without revealing sensitive information, ZKPs are poised to revolutionize various industries and reshape how data is handled and shared on the blockchain.
About Hypersign
Hypersign is an innovative, permissionless blockchain network that manages digital identity and access rights. Rooted in the principles of Self-Sovereign Identity (SSI), Hypersign empowers individuals to take control of their data and access on the internet. It provides a scalable, interoperable, and secure verifiable data registry (VDR) that enables various use cases based on SSI. Built using the Cosmos-SDK, the Hypersign Identity Network is recognized by W3C (World Wide Web Consortium), promoting a seamless and secure identity management experience on the Internet.
Get in touch with us today to understand the nuances of the decentralized identifier and their real-world application at meet.hypersign@gmail.com



















